I’ve been using WordPress since 2008. Throughout this time, I’ve been fortunate enough to never face a hacked or infected site of my own.
But luck is not a security strategy. While my experience has been secure, many WordPress site owners worry about hacking and infections, a genuine concern that drives the need for proactive security. The key principle here is that everyone online faces security risks.
There is no 100% security, and if you have a public site, you’re a target 24/7.
Attacks aren’t personal. They occur automatically and frequently. This is why you need a proactive, multi-layered security plan.
Securing WordPress takes more than just installing a security plugin.
Is WordPress secure?
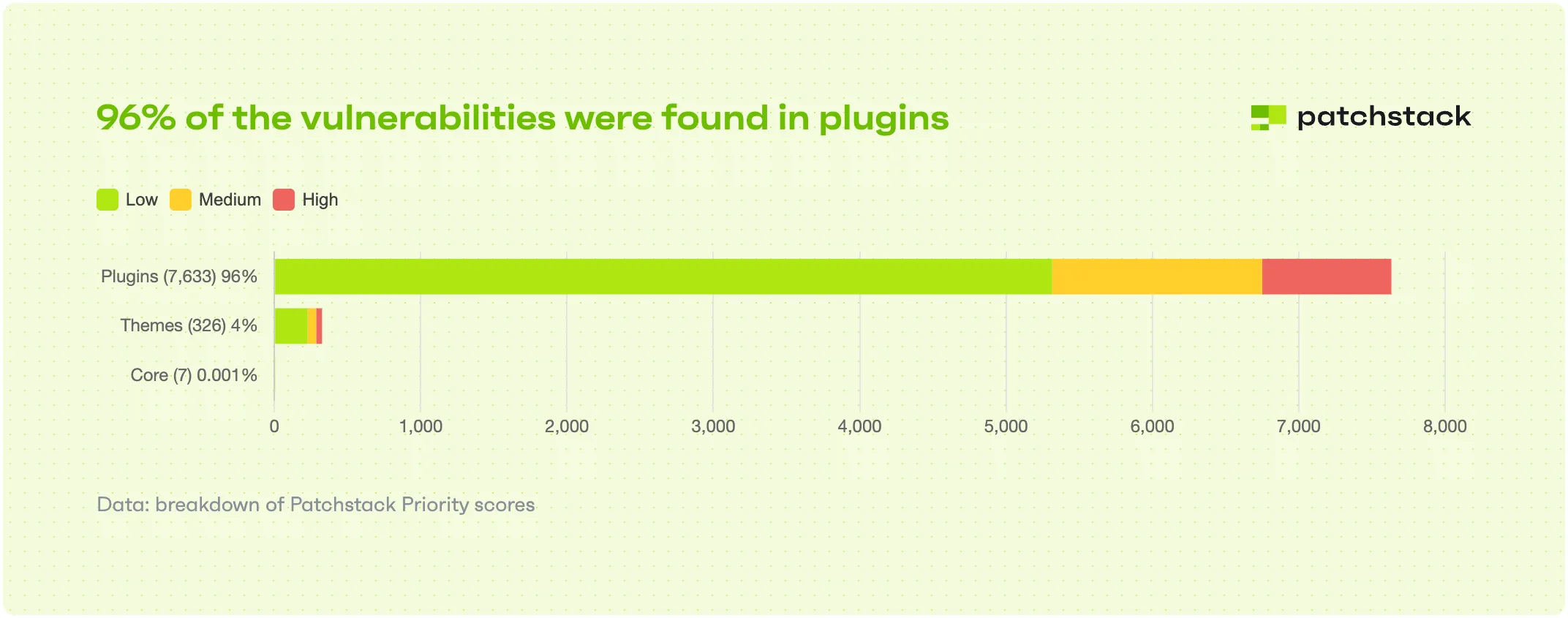
Yes, WordPress core is secure. Its popularity, though, makes it a prime target for attackers.
However, most vulnerabilities don’t stem from WordPress itself, contrary to popular belief.
- ~96% of vulnerabilities come from plugins
- ~4% come from themes
- Only 0.001% come from WordPress core
Source: State of WordPress Security 2025 (Patchstack)
This shows that our main responsibility is to properly manage the elements we add on top of the WordPress core; choosing high-quality plugins and themes and keeping them up-to-date is essential to securing WordPress.
What are the real causes of infections?
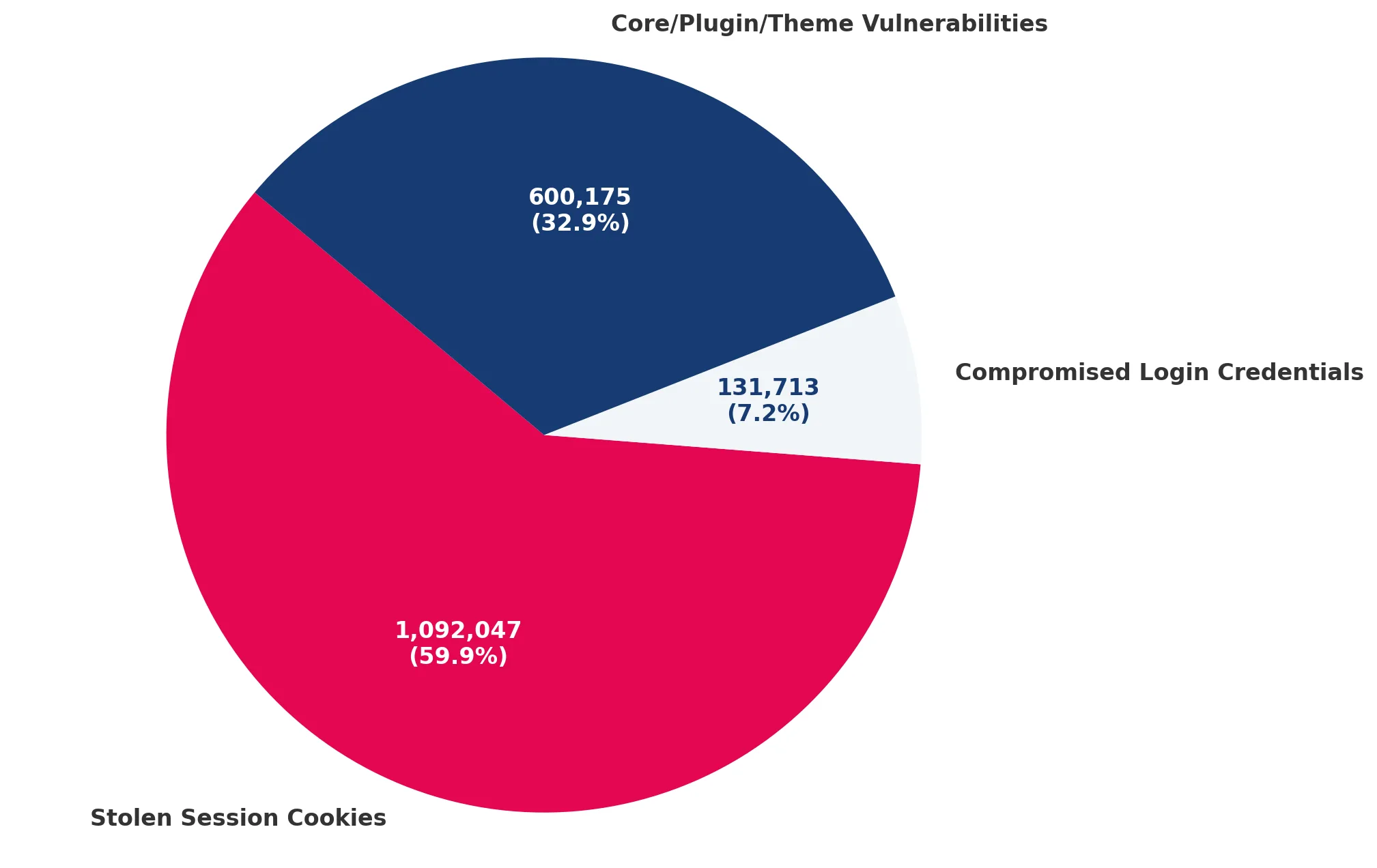
A study of 9.5 million WordPress sites found that the biggest risk is unauthorised access, not code vulnerabilities.
- 59.9% of sites were infected through stolen session cookies
- 32.9% through vulnerabilities in plugins and themes
- 7.2% through compromised access credentials
Source: We watch your website
With this in mind, protecting session cookies becomes essential to keep your site safe. If stolen, session cookies give attackers unrestricted access, bypassing all login methods.
Knowing this information, let’s see how we can secure our sites.
How to secure your WordPress website
Based on what we’ve seen, the top priority should be protecting session cookies. Session cookies are bits of data stored by your browser when you log into a site, and they help the website remember who you are during your visit.
These are obtained outside the WordPress ecosystem by infecting the administrator’s computer with malware that steals cookies from the browser.
If a session cookie is valid and has not expired, the attacker has full access, regardless of two-factor authentication (2FA) or other login protection methods. Once the cookie is obtained, the attacker can extend the session’s validity and maintain access to the site.
Our second priority is maintaining a clean and up-to-date WordPress ecosystem, ensuring no security vulnerabilities exist.
Let’s take it step by step.
Step 1 – Secure your devices
If your device gets compromised, your site is at risk, regardless of how well you’ve secured WordPress.
Let’s explore some practical steps to effectively secure your devices. By strengthening your device security, the risk of unauthorized access to your WordPress site will be greatly reduced.
The recommendations would be the following:
Use an antivirus/antimalware protection
Install a trusted security solution and run periodic scans to protect your system.
Malware on your computer can include a keylogger (which records everything you type, including passwords) or a stealer (specialising in stealing session cookies and saved passwords).
Even with a secure site, if your device is compromised, attackers can gain access. Use trusted tools like Bitdefender or Windows Defender, and keep them up to date. If unsure, start with Windows Defender on Windows, as it is reliable and built-in. Schedule a complete scan at least once a week.
Keep your system updated
Ensure that your operating system and web browser are up to date.
Updates aren’t just about new features. A large part of them contain critical security patches that close recently discovered “holes.”
Hackers actively exploit these known vulnerabilities on outdated systems to gain control over devices. Enable automatic updates for both the operating system and browser. It’s the simplest and most effective method to stay protected without constant effort.
Be careful with browser extensions
Many people don’t know what permissions they grant to browser extensions because they’re not careful, they quickly skip through installation.
If you read carefully, you’ll be scared, many extensions can read absolutely all page content, even the passwords you enter or card details when you buy something from a site.
A malicious extension, even if it seems harmless (e.g., a file converter or a video downloader), can steal session cookies, inject ads, or even modify your passwords in the background.
Only install extensions from official stores (Chrome Web Store, Firefox Add-ons). Before installing, check the developer’s name, read reviews, and look at the number of users. Perform periodic cleaning and uninstall extensions you no longer use.
Avoid public Wi-Fi networks
Don’t log into your site’s admin panel when connected to a public, unencrypted Wi-Fi network.
Wi-Fi networks in cafes, airports, or hotels are insecure by nature. An attacker connected to the same network can intercept unencrypted traffic using “Man-in-the-Middle” techniques.
Even if the site uses HTTPS, there are risks of being redirected to fake pages or having your data compromised. A much safer alternative is to use a hotspot from your mobile phone.
Don’t use public devices
Avoid accessing the site from public computers or other people’s devices.
You have no control over the software installed on a computer in a library, hotel, or internet cafe. These can have hardware or software keyloggers that record absolutely everything you do.
Even a friend’s computer can be infected without them knowing.
If you’re in an absolute emergency situation, use a private browsing window (Incognito), make sure you log out correctly, and most importantly, change your password as soon as you get to a trusted device.
Use caution online
Be extremely cautious of suspicious links and email attachments. Avoid free social media offers that may contain malicious scripts.
This is the entry point for phishing and social engineering attacks. An email that appears to be from a bank or social network can trick you into entering your data on a fake login page. A fun quiz on Facebook can request permissions that give it access to your personal data or can run scripts that compromise your browser.
Hover over links in emails to check actual destinations. Never download executable attachments from untrusted sources. Treat urgent messages with suspicion.
Always log out
When you’ve finished working, use the Log Out button.
Just closing the browser tab doesn’t invalidate the session cookie. The session cookie is a small file stored on your computer that tells the WordPress site you’re authenticated. This cookie remains valid for a period of time, even if you close the browser window.
If malware infects your computer during this interval, it can steal the cookie and use it to access your site. The Log Out action sends a signal to the server to immediately invalidate that cookie, making it useless.
Form this habit. Think of the “Log Out” button as locking your house door when you leave. It’s a simple, quick gesture that adds an essential layer of protection.
Conclusion
Start implementing these recommendations today to safeguard your WordPress site and protect all your users.
These rules apply to all users who have access to the site, regardless of access level. A compromised author account can become an entry point for an attacker, especially if there’s a privilege escalation vulnerability on the site.
If a user’s session cookies are stolen and the site has a WordPress plugin installed with a vulnerability that allows privilege escalation, then it’s possible for the attacker to obtain administrator privileges through that user, even if that user wasn’t an admin.
After ensuring your device is clean, the next step is to protect access to the site.
Step 2 – Secure access to the WordPress admin
The next step in protecting your WordPress website is to secure admin access by managing users and permissions, enforcing strong passwords, and restricting access.
The recommendations would be the following:
Use unique usernames
Never use generic usernames like “admin” or ”administrator”. For example, I use obscure footballer names from Pro Evolution Soccer, like Momo Bojang and Afimico Pululu.
Brute-force attacks often try “admin” as the first attempt, and forcing attackers to guess your username raises the difficulty.
If your site already has an “admin” account, the correct and safe procedure is as follows:
- Create a new user account with Administrator role and a unique name (momo_bojang, afimico_pululu, etc.)
- Log out of the “admin” account
- Log in with the new administrator account
- Go to the “Users” section and delete the old “admin” account
Warning: WordPress will prompt you to decide what to do with content created by the “admin” user. Choose the option “Attribute all content to:” and select your new account.
This way, you won’t lose any articles or pages.
Pro tip: You can have a user with administrator privileges, which you use only for administrative operations on the site. For content published on the site, consider having a user with only author privileges.
Use complex passwords
Use passwords of at least 12-16 characters, combining uppercase letters, lowercase letters, numbers, and symbols. A password manager (integrated in the browser or a dedicated application) is your best friend.
Length is often more important than complexity. A password like password123! can be cracked in a few seconds. A password like MyDogEatsGreenBiscuits! is a “passphrase” that, although easy for you to remember, would require many years to be cracked by a computer through brute force.
Ideally, combine length with complexity. Using a password manager (e.g., Bitwarden, 1Password, Proton Pass, or those integrated into modern browsers) completely eliminates the headache.
These tools do three essential things:
- Generate extremely complex and long passwords (ex: g7#kP$zV9@rT!nE*)
- Save these passwords in an encrypted digital vault.
- Automatically fill in login details, so you never have to memorise them.
This also prevents password reuse, one of the biggest security mistakes.
Make a periodic audit
Regularly check the user list and delete inactive or suspicious accounts.
Ensure each user has the role with the minimum privileges necessary for their activity. Each user account is a potential “door” into your site. Old, forgotten accounts of former employees or collaborators represent a major security risk.
If the password associated with such an account is weak or if the email address was compromised elsewhere, the account can be taken over and used to attack the site.
Apply the “Principle of least privilege“.
Set a calendar alert once every three months to do the following check: Go to Users -> All Users. Review the list and delete any accounts that are no longer needed. For the remaining accounts, analyse each one’s role. An author only needs the Author role. Someone editing others’ content needs the Editor role.
Grant the Administrator role only to those who absolutely need to install plugins and themes and modify the site’s basic settings.
Hide the login URL
Changing the login address to a custom one can significantly reduce the number of automated brute-force attacks.
The address yoursite.com/wp-login.php is the universal standard for WordPress, known to all attackers and bots.
They constantly attempt to access this address, consuming your server resources and attempting to guess passwords. By changing this address, bots will encounter a non-existent page (“404 Not Found”), and their attack will be halted before it begins.
Changing the login address is similar to moving your front door to a secret location. A dedicated plugin can make this easy. Try a lightweight plugin like WPS Hide Login, which specialises in this one task and does it exceptionally well.
After activation, go to Settings -> General and scroll to the bottom of the page. You’ll find a new option called “Login URL“. Enter something unique and memorable for you (like access-panel, secret-entrance, portal). Save the changes.
Implement 2FA – Two-factor authentication
Even if your admin password is stolen, 2FA adds a second layer of protection (a code generated by an app on your phone), blocking unauthorised access. Enable 2FA for all administrator accounts and, whenever possible, all users with sensitive roles.
A simple WordPress plugin that does just this is Two-Factor. Another plugin that offers more options but remains focused on securing authentication is Fluent Auth.
Protect against brute-force attacks

You can limit the number of failed login attempts to block automated attacks.
A “brute-force” attack is exactly what the name suggests: a software robot tries thousands or millions of password combinations per second, hoping to hit the correct one. Without a protection measure, this process can continue indefinitely.
Besides the obvious security risk, these attacks consume enormous processing resources (CPU) on the server, which can lead to slowdowns or even block legitimate visitors from accessing your site.
A login attempt limiting plugin works like a guard. After a preset number of incorrect attempts (e.g., 3 or 5) from a specific IP address, the plugin temporarily blocks that IP address for a specified period (e.g., 30 minutes or longer).
WordPress plugins that can help:
Monitor website activity

It’s essential to know what’s happening on your website.
Think of an activity log as your site’s surveillance camera system and a “black box.”
While it does not directly prevent incidents, an activity log is essential for understanding what happened after an event, whether it is a security attack, human error, or a technical issue. Without this log, investigating a problem is like searching for a needle in a haystack while blindfolded.
The Stream plugin, for example, should be essential on any site accessed by multiple people. It chronologically records critical actions such as:
- If a new user with the administrator role was created
- Who logged in and when
- What plugin was activated or deactivated and by whom
- What article was deleted, and by whom
You can configure email alerts for the most critical events in the plugin. You can get an instant notification whenever an administrator logs in or when a plugin is installed. This can provide the warning you need to react quickly in case of unauthorised activity.
Use session control
For advanced control, actively manage user sessions to ensure strict security.
A “session” represents each active login to your site. You can be simultaneously logged in from your office computer, home laptop, and phone. Each of these is a distinct session, validated by a cookie. If any of these cookies is stolen, the attacker can use that session to access the system.
Session control provides visibility and control over active connections. Using a plugin like Sessions (from the PerfOps One suite), you gain direct control: you can see in real-time who is logged in, from what IP address, and for how long.
A simultaneous login from your city and China for the same user is a clear alarm signal. If you notice a suspicious login session, you can close it instantly with a single click. This action invalidates that cookie and logs out the attacker.
You can set a rule preventing a user from having more than one active session. When they log in from a new device, the old session is automatically closed. This simple measure drastically reduces the attack surface, eliminating the risk of “forgotten” cookies on various devices.
Restricting access through IP
If you’re the only person administering the site, you can block everyone’s access to wp-admin and wp-login.php except your IP address.
In this case, even if your password is cracked or your session cookies are stolen, the attacker can’t log into the site. If you have a dynamic IP address, this method may not be practical, as your IP address can change frequently, potentially locking you out of your own site. Consider using alternative methods for access restriction that accommodate dynamic IPs, such as VPNs with a static IP or IP whitelist services.
The blocking can be done from the .htaccess file. You add the following code (replace YOUR_IP_ADDRESS with your IP address, which you can find by accessing our tools site from your device):
order deny, allow
deny from all;
allow from YOUR_IP_ADDRESSGood, we’ve addressed the main cause of infections so far, which is authentication compromise (stolen session cookies + compromised credentials).
Let’s continue addressing the second cause, exploiting vulnerabilities in plugins and themes.
Step 3 – Constant maintenance (updating and cleaning)
Once access to the WordPress admin interface is secured, we need to ensure that the site’s software has no security vulnerabilities or “cracks.”
Update everything, always
The lifecycle of a vulnerability is a race against time. Once a security issue is discovered and a patch is released, details about the vulnerability often become public. Hackers then start scanning thousands of sites to find those still running the old, unpatched version.
For most small sites that use only a handful of carefully selected plugins and a high-quality theme, enabling automatic updates works well.
WordPress allows automatic updates for minor core versions. You can also enable automatic updates for WordPress plugins and themes directly from the admin panel or through the WordPress management tools integrated into your hosting provider’s control panel.
Automated updates reduce the need for manual intervention; however, we recommend setting up an uptime monitoring service to ensure you’re notified if an update causes an issue.
For more critical sites, manual control over how and when updates are made is preferable.
Use a staging environment
A staging environment is a vital tool for testing and development purposes.
It’s a clone of your live site where you can safely test major updates, new plugins, or code modifications. If something breaks on staging, it has no impact on your visitors. Performing updates directly on a live site, especially one that generates revenue, is an unnecessary risk, so make sure you use the staging platform offered by your hosting provider.
It’s easy to create a clone of your website on Kiravo (follow this tutorial), allowing you to make updates safely without affecting the live site. If everything works without problems, you can apply the updates in production.
If your hosting provider does not offer built-in staging options, a plugin like WP Staging can be an effective solution; however, it may add some bloat to your website.
Make backups before any changes
A good practice for updates or modifications to the code or database is to make a backup beforehand.
An update can fail due to incompatibility with another site component, leading to critical errors (such as a “white screen of death”). Without a recent backup, recovery can be stressful, costly, and lengthy. With a backup, you can return to the functional version of your site in a few minutes.
At Kiravo, we offer automatic daily backups and the ability to create manual backups directly from the control panel. Both automatic and manual backup options are available across all our hosting plans.
Delete what you don’t use
A frequently overlooked aspect is removing unused plugins and themes.
It’s essential to understand the difference between “inactive” and “deleted”. An inactive plugin or theme is like an installed but not running program. Its physical code still exists on your server. If that code has a vulnerability (for example, a script that can be accessed directly through a specific URL address), an attacker can exploit it regardless of whether the plugin is activated or not.
Each software element you keep adds to your site’s “attack surface”; more code means more potential entry doors. Ask yourself: “Is this plugin/theme absolutely essential for my site’s functioning NOW?“.
If the answer is no, first deactivate the element. Then, navigate the site to make sure everything works correctly. If everything is fine, come back and delete it permanently.
Give up the “I might need it sometime” mentality. If you need it again, you can reinstall it in 30 seconds. The security risk of keeping unused code far outweighs the minor inconvenience of a future reinstallation. The golden rule is: if you don’t use it, delete it!
This applies not only to themes or plugins, but also to entire sites – don’t leave old sites, test sites, clones, outdated stagings, or anything else you don’t actively use on the server, especially if you have a classic cPanel hosting plan, where there is no isolation between sites.
Monitor errors
Another important aspect is monitoring error logs after updates have been applied.
Sometimes, an update doesn’t crash the site but introduces “silent” PHP errors running in the background. These errors can slow down the site’s performance, cause abnormal functionalities, and fill up server space with log files of tens of gigabytes. Checking the error log is like a medical checkup after an intervention.
After performing updates, access the file manager from the hosting panel and locate a file named error_log (typically in the site’s root directory). Open it and look at the latest entries.
These can alert you to any problems that have occurred and help you resolve them.
Watch out for shared hosting!
On a cPanel account, sites are not isolated from each other.
A vulnerable or infected site can compromise all other sites in the same account. Ensure that all sites you manage are equally well-secured.
Pro tip: Don’t host sites of friends, family, or any other site you don’t control on your cPanel account. If any of them have security problems, vulnerabilities, or infections, it can affect all your sites.
Sites on the Kiravo hosting platform are isolated from each other, so an infected site cannot infect another site.
By keeping all PHP scripts up to date on all sites, you’ll significantly reduce the risk of your site becoming a victim of software vulnerability-based attacks.
Block malicious traffic before it reaches the server
A reverse proxy service, such as Cloudflare, acts as an intelligent shield placed in front of your server, which filters malicious traffic before it reaches your site. The most popular services offering filtering and protection solutions are:
Traffic passes through their global network, where it can be filtered based on IP, country, request type, suspicious behaviour, presence of bots, or traffic intensity.
I’ve been using Cloudflare’s free plan for my websites for a long time, and it has been sufficient to provide adequate protection.
What you can do from Cloudflare to secure your WordPress site:
- You can block traffic from high-risk regions (e.g., China, Russia, etc.)
- You have free, automatic, and unlimited DDoS protection
- You have protection against bots scanning the site
- You can protect contact forms with Cloudflare Turnstile
- You can block or limit access to PHP files that are frequently attacked (e.g.,
xmlrpc.php)
Bonus – The right hosting partner
This is where the major difference lies between cheap hosting and premium hosting specialised in WordPress.
Quality hosting will offer server-level WAF, real-time anti-malware scanning, and IP blocking as standard. Even a cheap one offers those benefits.
But a premium hosting like Kiravo will go further:
- site isolation – each site runs in its own isolated container. On the same hosting package, you can have sites on different servers, in different locations.
- auto-repair for WordPress core – modified or infected WordPress core files are automatically replaced with clean versions.
- login protection through a captcha solution + limiting failed login attempts and blocking automatic logout from admin after 60 minutes of inactivity
- security headers – prevent vulnerability exploitation, protecting against Cross-Site Scripting (XSS), clickjacking, and other threats.
- uptime monitoring – hosting providers typically only monitor their servers, not clients’ sites. Kiravo also monitors sites to enable quick intervention during downtime (caused by infections or other issues).
- proactive expert support – it’s easy to throw an AI chatbot to answer basic questions, but in case of a complex malware attack, you need experts on your side.
These benefits are near impossible to obtain on cheap cPanel hosting.
Myths and realities about WordPress security
Many “tips” you see online are either outdated or completely useless. Let’s review a few frequently found in superficial and poorly documented articles, which either bring no real benefit or induce a false sense of security.
Myth: WordPress is insecure
Reality: WordPress core is very secure.
According to the Patchstack report for 2024, 0.2% of vulnerabilities were found in WordPress core. In the 2025 report, the figure dropped to 0.001%—only 7 vulnerabilities. Risk comes almost exclusively from poor quality, outdated themes/plugins, or wrong usage practices.
Myth: You need an “all-in-one” security plugin
Reality: these monolith plugins can offer a false sense of security.
Intelligent malware can easily fool a local scan, and some of these plugins have had serious vulnerabilities themselves. Moreover, they consume significant resources. It’s more efficient to use small, specialised plugins (for 2FA and login limiting) and leave scanning and firewall protection to the hosting provider and an external service, such as Cloudflare.
Myth: My site is small, so nobody attacks me
Reality: the vast majority of attacks are automated.
While a more well-known site has a higher chance of being attacked, bots constantly scan the internet looking for vulnerabilities, not just famous sites. Your site is just an IP on a list.
Myth: HTTPS secures my site
Reality: partially true.
HTTPS encrypts data in transit, protecting information sent through forms. It doesn’t protect the site from malware, SQL injections, or software vulnerabilities. It’s a necessary but small piece of the security puzzle.
Myth: I have good hosting, so I don’t need to worry
Reality: partially true.
Ordinary hosting, no matter how good, provides a solid foundation, but it cannot secure your site’s code, weak passwords, or vulnerable plugins you install. It’s a trustworthy partner, but doesn’t do all the work for you.
Myth: I changed the database prefix, so I’m ok
Reality: a completely useless measure in practice.
The default prefix for database tables is wp_. You’ve probably seen recommendations to change it to something custom. It’s one of the most useless suggestions. Database security doesn’t lie in a weird prefix. Don’t waste your time with that; it has no relevance.
Myth: Hide WordPress version
Reality: Irrelevant.
Bots will try to exploit all known vulnerabilities, regardless of the version you report in the site’s header.
Conclusion
Securing a WordPress site is not something you do just once; it is an ongoing process that requires regular attention and care.
By employing a layered approach that incorporates good digital habits, robust access controls, regular updates, an external firewall, and high-quality hosting, you can reduce risks and establish a rock-solid foundation for your online presence.
Do you have questions or need help securing your WordPress site?
Feel free to contact us. We offer security audits and malware removal services at affordable rates. If you’re a Kiravo customer, our support includes malware removal at no additional charge.
Leave a Reply